Balkan OI '11 P2 - Decrypt
View as PDFThere is a rumor that the Scientific Committee is using a special device for encrypting their
communication. If you can crack the encryption you could listen to the problems they have prepared
and score many points. Last night you got lucky: one of the members forgot their device in a bar.
You opened it and looked at the general design:
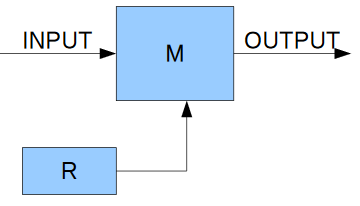
All the operations use 8 bits. XOR is the bitwise exclusive
or function (the ^ operator in C, xor operator in Pascal).
is a sequence of pseudorandom numbers defined as follows:
,
and
have secret values only known by the Scientific Committee.
- For
let
.
Furthermore, we have a function ,
. In fact,
is a bijection, i.e. when
it must also be that
.
The device used by the Scientific Committee takes one number at a time, and outputs it encrypted.
After using the device times, the next number,
is encoded as follows:
Even though you understand how the encryption device works, you do not know the secret values
,
, and
. Also, you do not know
, so you cannot decode the communication. What you can do instead is play with the device you found. You can give it input numbers and observe the outputs.
Task
Your task is to find out all the secret values: with less than
queries (input numbers).
Constraints
- A correct solution receives points only if the number of queries is less than
.
- In all tests the secret keys
are random.
Interaction
This is an interactive program. To play with the encryption module simply write a number between
and
to the standard output. You can then read from the standard input the output of the
encryption device, also an integer between
and
. When you know the secret values output one
line containing the string
SOLUTION and after that output lines:
, one value per line.
Example
Let's assume that ,
,
and that
.
From here we deduce .
| Contestant output | Contestant input | Comments |
|---|---|---|
| 10 | 11 | M[10 XOR 0] = M[10] = 11 |
| 10 | 12 | M[10 XOR 1] = M[11] = 12 |
| 11 | 9 | M[11 XOR 3] = M[8] = 9 |
| 12 | 14 | M[12 XOR 1] = M[13] = 14 |
| ... | ... | |
| SOLUTION 0 1 3 1 2 3 4 ... 254 255 0 | When you find out the secret values you output them. |
Comments